Introduction
This article is mainly written for beginners stepping into the world of cybersecurity. When you start your journey, you’ll come across a flood of hacking tools and it’s totally normal to feel overwhelmed or wonder, “Do I need to learn everything before getting started?” I’ve been there too. I had the same doubt, but thankfully, some of my friends helped me understand the real path and what truly matters in the beginning.
In this article, we’ll explore some essential tools every beginner hacker should know about, along with their real-world uses.
Disclaimer: This article is for educational and legal purposes only. We do not promote or support any illegal activities
Tools:
1. Nmap (Network Mapper)
Nmap is a security tool used during the port scanning phase of penetration testing. It helps identify open ports on a target device, along with the services and their versions running on those ports. Nmap offers a wide range of options that can enhance your scanning process—for example, some scripts can even detect vulnerabilities in the discovered services.
It’s also capable of discovering active hosts within a subnet and listing them. If you’re a beginner in cybersecurity, this is one of the first tools you should learn. Nmap is crucial for network penetration testing and is often the starting point in most TryHackMe and HackTheBox rooms.
We can take a look at how host discovery works in Nmap, the commands used, and the kind of results it gives:
nmap -sn [192.168.1.0]/24
Here,
nmap – This part calls the Nmap tool.
-sn – This option tells Nmap to skip the port scan and only perform host discovery (ping scan).
192.168.1.0/24 – This is the subnet we are scanning.
192.168.1.0/24 is the network address
/24 indicates the first three part of the local ip address shows the network which we want to scan and this helps the tool understand we are going to scan whether the devices from the range of 192.168.1.1 - are online or not.192.168.1.254

This is a simple example you can try, and there are a lot of features in it. Since we are not only writing about Nmap, I can’t go through all of them here. So, explore it yourself and use the official Nmap site to get more information about the tool.
Official Site: nmap
2. Burp Suite
Another must-have tool in a beginner hacker’s kit is Burp Suite Community Edition — yes, it’s the free version of the professional tool. Burp acts as a proxy that intercepts the traffic between your browser and the target website.
This is super useful because many developers rely only on browser-level restrictions and assume users will interact with their site only in normal ways. But by using Burp, you can see and modify the raw requests, helping you bypass client-side restrictions and uncover hidden vulnerabilities. It is used for penetration testing of web applications. It is developed by a company called PortSwigger, and they also provide a free training course on web application penetration testing, which is very useful. This is also one of the cybersecurity tools that has a clean Graphical User Interface.
Main Features in the Burpsuite:
- Burp Proxy and Interceptor: This is one of the primary features in the Burp Suite software. It acts as a proxy server for client-side HTTP requests, allowing you to edit the values in the request after the browser sends it and before it reaches the server.
- Burp Repeater: As the name suggests, it repeats the captured HTTP request. It allows you to experiment with various changes easily and helps you find what you’re looking for.
- Burp Intruder: It is used to inject payloads into various parts of a website where we want to test for vulnerabilities.

Official Site: burp
3. Metasploit Framework
Metasploit Framework is a powerful hacking tool. As the name suggests, it’s a framework that allows you to search, configure, and launch exploits against vulnerable systems. It includes features that let you scan, exploit, and even perform post-exploitation on a target if any vulnerabilities are found.
It’s another must-know tool for hackers, working entirely through the CLI (Command Line Interface). Metasploit is mainly used in the exploitation phase of a penetration test, where the attacker tries to gain control over a system by targeting known vulnerabilities.
What can we do with this:
Search: we can search for exploits for a known version which we get from nmap.
search [service with version]
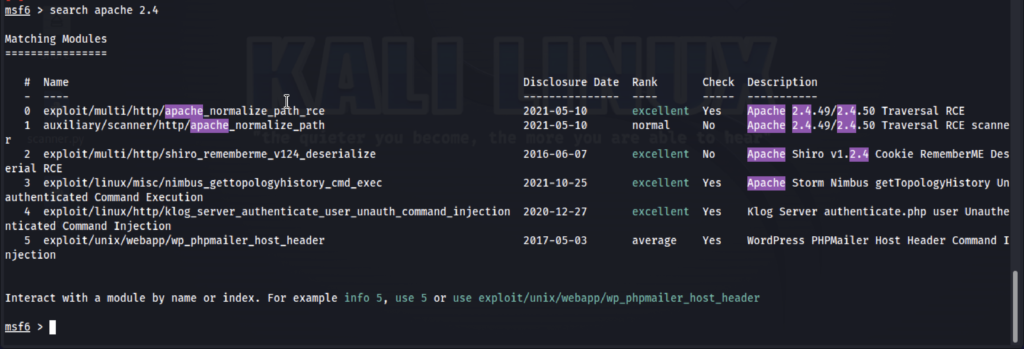
It will list a variety of exploits and other modules available in the framework.
Lauch Exploit: After identifying a vulnerable service, we can launch a suitable exploit by loading it into the framework and delivering it to the target to gain access.
use [ # number ]
or
use /path/name
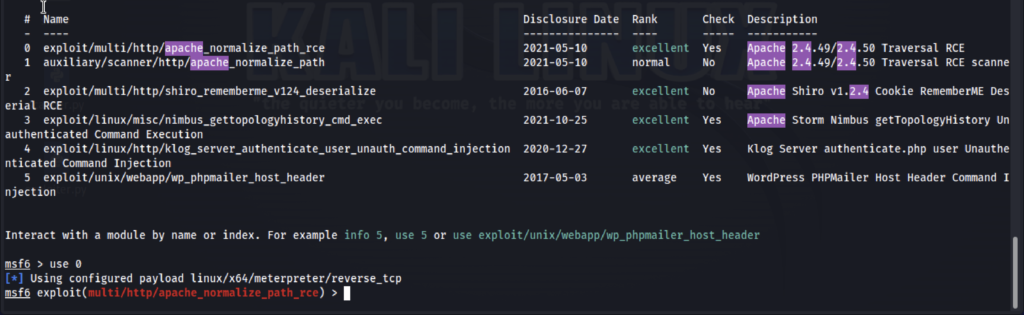
Payload Management and Post-Exploitation are other important features and modules available in the framework.
Official Site: metasploit
4. Gobuster
Gobuster is an enumeration tool used to find hidden endpoints or directories on a website. Its working logic is very simple but powerful, especially when you’re trying to discover useful or hidden web paths that may lead to vulnerable pages.
The core logic of Gobuster is straightforward. For example, let’s say our target site is https://strawhathackers.com/ and we want to find hidden or potentially interesting pages that might give us an advantage while trying to hack the site. If we have a wordlist or a file containing possible endpoints like:
/admin.php
/admin
/login
/hidden-one
Gobuster will go through each of the endpoints in the wordlist, and based on the HTTP status codes returned, it will display the potential valid endpoints. It typically ignores 404 responses and highlights those that return 200 (OK) or 301 (Redirect), as these indicate the endpoint likely exists.
gobuster dir -u [site url] - w /path/to/wordlist
Here,
gobuster – This calls the tool
dir – This tells Gobuster to use directory/file brute-forcing mode.
-u – u stands for url and this option will help the tool identifying the url user inputs.
-w – w stands for wordlist, indicating the path to the wordlist stored on the system, which the tool uses for brute-forcing.

Official Kali Site: gobuster
5. Hydra
Hydra is a powerful brute-forcing tool that you can use in CTFs or real-world hacking scenarios. Like the tools we mentioned above, it’s also easy to use and helps make your work more efficient.
Brute-forcing is the method of trying different passwords for a known username or trying various usernames to find the correct one. For example, imagine you have a phone with a 4-digit number lock (with no mechanisms to prevent brute-forcing). You know the password ranges from 0000 to 9999, so it’s just a matter of finding the exact one. In such cases, brute-forcing is possible. Hydra will automatically try all combinations from 0000 to 9999 and identify the correct one by testing each possibility.
We can use Hydra to brute-force services like SSH, FTP, web login pages, and more.
hydra -l admin -P /usr/share/wordlists/rockyou.txt ftp://192.168.1.100
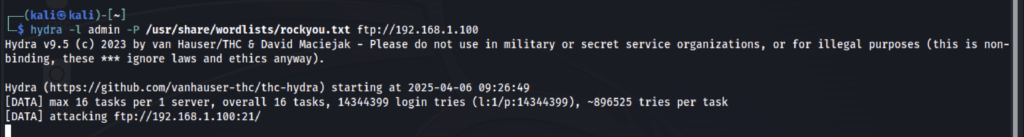
Here,
hydra – This part is used to call the hydra tool.
-l admin → Single username to try (admin). Here, the brute-forcing is done to unlock the admin user account by trying passwords from the wordlist named rockyou.txt.
-P /usr/share/wordlists/rockyou.txt → Path to your password list.
ftp://192.168.1.100 → Target IP using the FTP protocol
Official Kali Site: hydra
6. John The Ripper


Here is another name you will never forget. John is used for password cracking but mainly focuses on the cracking of hashed passwords. It uses a dictionary or wordlist to compare the hashes, as cracking a hash by reverse method is impossible, and compares the hashes to find the associated or real values before the data was hashed.

john --wordlist=/path/to/the/wordlist.txt --format=raw-md5 hash_file.txt
Here,
john – This is used to call the tool.
-wordlist=/path/to/the/wordlist.txt – As the name indicates, it’s the path to the wordlist used by John to crack the hashes.
--format=[type] – Specifies the hash type we are trying to crack.
hash_file.txt – The file that contains the hashed password we want to crack.
Since John’s job is to crack hashes, it becomes extremely useful whenever you come across any hashed data. So next time you see hashes, call JOHN!
Official Site: John
7. theHarvester
theHarvester is a tool used during the Reconnaissance phase of penetration testing. It’s an OSINT tool that helps us collect publicly available information about our target. It helps us find the target’s email addresses, subdomains, IPs, employee names, and hostnames from public sources like Google, Bing, LinkedIn, Yahoo, Baidu, and more.

theHarvester -d [sitename] -b all
Here,
theHarvester – This part is used to call the tool.
-d sitename – Target domain.
-b all – Data source(includes Google, Bing, Yahoo, LinkedIn, Baidu, and more)
Github Link: theHarvester
8. Nikto
Nikto is a free, open-source, command-line-based web server vulnerability scanner that checks for and finds dangerous files, outdated software, insecure headers, and other misconfigurations. This tool is loud and fast, perfect for quick scans.

nikto -h [siteurl]
Here,
nikto – This calls the Nikto tool.
-h [site url] – This is used to mention the site (URL or IP) that we want to scan.
We can also mention ports using the -p <port> option, and there are many other options, explore them yourself using the documentation or other resources.
Github Link: nikto
Conclusion
Here, we explored and learned about some important tools for beginners and their use cases in real-life scenarios. This is not a complete list, there are many more tools out there, and new ones are constantly emerging. Cybersecurity is a field of continuous growth, so this list reflects the tools currently valid in 2025. While things may change, this will definitely be useful for any beginner starting out this year.
Leave a Reply